Orchestrated Authentication
Secure AI Workflow Collaboration
Sam Liu - Software Engineer at Thread AI
Quin Burke - Software Engineer at Thread AI
November 04, 2025
For years, enterprise access control followed a predictable script.
A human-centric security framework, built on the pillars of Identity Providers (IdPs), Role-Based Access Controls (RBAC), and Multi-Factor Authentication (MFA), served as the bedrock of enterprise security. This world operated within defined swim lanes, with policy-driven tools creating a logical, auditable framework that tied every action back to a verified human user.
That world is changing. Its logic is no longer confined to human users. A new class of digital workers is proliferating across every organization: Non-Human Identities (NHIs) - comprised of everything from service accounts and API keys to the sophisticated AI agents now being deployed. According to Gartner1, these NHIs outnumber human identities by over 45 to 1, with others claiming it's well over 100 times.2
The most profound security shift undoubtedly comes from AI-powered agents. Unlike a predictable service account, agent actions can be dynamic and non-deterministic, creating an entirely new set of challenges. These agents don't just fetch information: they can execute complex, multi-step processes, access sensitive data, and take actions within the same enterprise systems used by human workers. This new class of identities, operating alongside human workers, requires a new playbook - one that confines agentic sprawl, preventing unnecessary permissions, limiting their sessions, and fundamentally segregating credentials from the agents themselves.
A new identity security mindset is mandated. How do you govern a machine identity that can dynamically change its actions based on new inputs? How do you manage credentials securely across dozens of integrated systems?
AI Enablement via Secure Workflow Shareability
This promise of new efficiency has fueled a generation of tools for building autonomous workflows, targeting both technical and business users. Some software vendors promise simple copy / paste mechanisms for sharing multi-step AI workflows. However the promise of shared autonomous and dynamic workflows in an enterprise is not without serious challenges. True collaboration isn't just about sharing logic; it's about sharing logic with the right access, securely.
When a workflow touches mission-critical systems, you often need more than a simple authentication model or developer debugging logs; you need a complete, auditable record of every action by both systems and humans and data access points. You need built-in access guardrails, policies around credential transfer, and the ability to strictly control what information is exposed to the AI model itself.
Even more critically, how do you unlock the true, compoundable value of AI, allowing workflows built by one team to be securely used by another, without creating major security vulnerabilities?
At Thread AI, we believe the answer lies in elevating authentication from a simple gatekeeper to a first-class pillar of the orchestration engine itself.
Our Philosophy: Auth as a Woven Fabric
Security can't be an afterthought bolted onto an AI workflow; it must be woven into its fabric. Our platform, Lemma, was designed from first principles with this philosophy in mind. We provide a unified control plane that governs the complex interplay between human users, AI agents, and the systems they access.
Our approach to orchestrated auth (authentication and authorization) defines these interactions.
1
Taming the Agent
Governing the Non-Human Identity Lifecycle and Actions
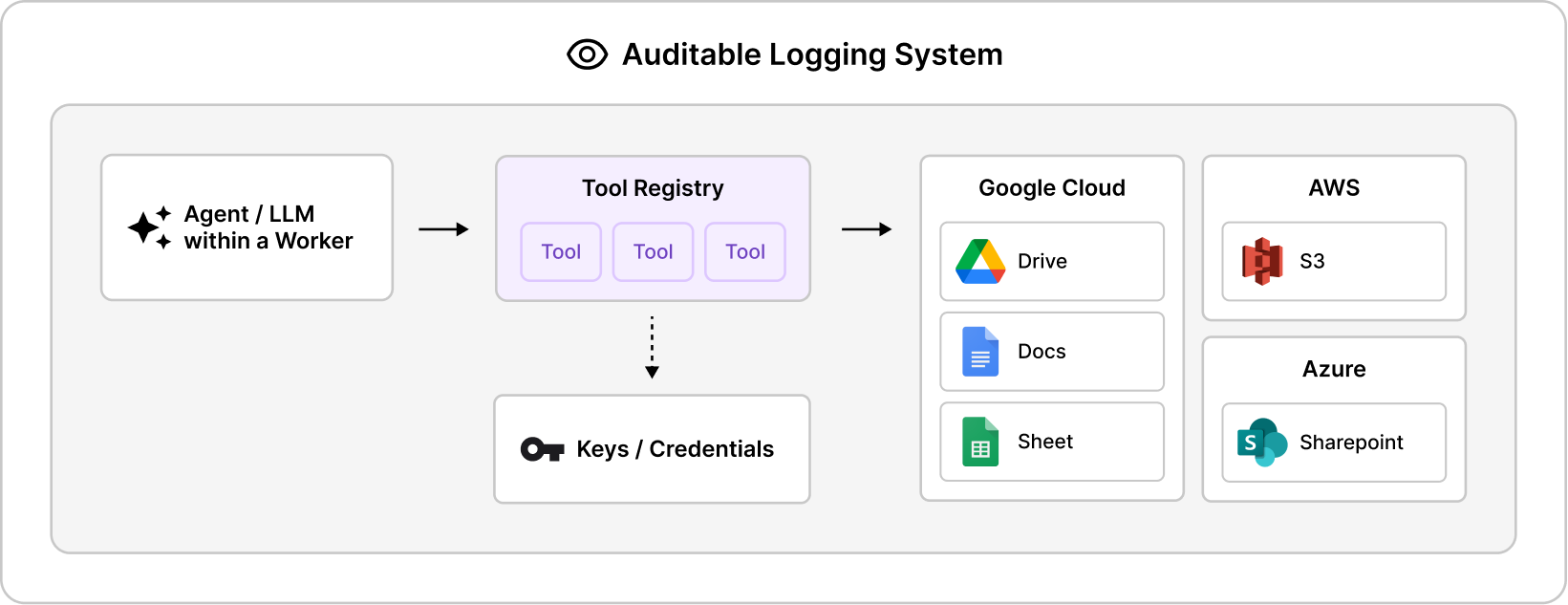
An AI agent's power comes from its ability to interact with other systems, but this is also its greatest risk. To securely enable these interactions, we defined set guardrails that allow management as well as full observability and auditability into AI actions.
Secure Secret Management
Keys and credentials are securely managed within Lemma's Secret Manager and are fundamentally decoupled from workflow logic. A workflow doesn't "know" an API key or a user password. Instead, functions are configured with keys and credentials within the Function Registry, tying them to the specific tool they access. When a workflow runs, it is granted temporary, scoped access to that credential and only for the duration of its task. This just-in-time access limits secret proliferation and eliminates hardcoded workflow-owned credentials, dramatically reducing the attack surface.
Curated Access to Tools and LLM Inputs
Agentic behavior can be unpredictable. To manage this, our AI Configuration layer acts as a strict, declarative gatekeeper for every tool function and data point that can be accessed by the agent. This layer also acts as a middleware for MCP servers and A2A interactions (Model Context Protocol and Agent-To-Agent, respectively), explicitly defining the access permissions for each. This means that before an LLM is ever prompted, you define an explicit "allow-list" of functions it is permitted to discover and invoke. This selection determines the data ever shared with the agent as well as prevents any malicious attempts to use unauthorized tools. These restrictions ensure it can only operate within clearly set boundaries.
Comprehensive Observability
Every workflow running on the Lemma platform is documented in an immutable logging system, allowing full observability over every interaction the AI has made within and across the organizational systems. Admins have visibility into who initiated or what triggered the workflow, what data was shared, which systems it interacted with, and what the outcomes and prompt definitions are for every step in the process, providing complete visibility for security, compliance teams, and auditors.
2
Incorporating the Human
Integrating with Enterprise Access Reality
We believe that cutting-edge technology should not demand blowing up your existing tech stack. Lemma is built to meet you where you are, seamlessly integrating with the security infrastructure you already trust.
Secure, Abstracted Execution
This integration with your IdP-synced groups is the foundation for Lemma's collaborative security model. The platform is designed to abstract capabilities: a user, like a team lead, can configure a Worker with a specific credential (e.g., a team service account) and then share that Worker with their team.
This is where the RBAC policies become critical. They allow only verified users to only view or run specific Workers they are entitled to. When they execute the Worker, the platform securely fetches the original, embedded credential (which the invoker cannot see) to perform the task.
This model enables a power user to securely abstract a high-privilege capability and provide it as a simple, auditable function to a broader team. You don't need to provision ten new people with sensitive database access; you just grant those ten people "run" permission on the Worker that already has it. Additionally, by leveraging this model, teams can build and collaborate on specific workflows and agents, thereby compounding their value, while designing others that are confined to only certain users.
Bridging to Your IdP
We use the SCIM protocol (System for Cross-domain Identity Management) to sync with your existing Identity Provider (IdP), such as Okta or Entra ID. Leveraging role-based access controls (RBAC) to mirror your established user groups and permission hierarchies within Lemma. Thus, the 'Finance Team' group you defined in your IdP is mirrored in Lemma, allowing you to apply consistent RBAC policies to that group without recreating complex permission structures - ensuring a single source of truth for user identity and access rights.
Setting Access Policies
This model of abstracted execution is critical because not all Workers are created equal. Some run daily processes, like sending meeting summaries, updating a CRM, or crafting emails, while others run mission-critical processes such as automated claim processing, tailored proposal crafting, or executive performance report preparation. Defining access for both the user (who can run it) and the agent (what it can access) is critical. With Lemma, administrators can determine who can access or trigger a workflow, who can share keys and credentials, and which mission-critical Workers will be visibly confined to only a subset of privileged users.

The Compoundable Value of a Shared Platform
The aforementioned guardrails for both human and non-human identities are the key to unlocking secure, cross-functional workflow collaboration and are the foundations that make AI transformation possible in an enterprise environment.
Still, we believe that for true business transformation, siloes have to be broken. Sharing workflows across teams of multiple functionalities and allowing each to benefit from what others have built is the only way to compound AI investment and speed time-to-value. Our platform enables reusability for every component, from context-aware functions or human-in-the-loop feedback (HITL) to complete end-to-end workflows.
Every set piece can be re-leveraged to solve a different problem or to streamline another process, making every new Worker easier and faster to build. This shared approach empowers businesses to shift their mindset, implementing a foundational orchestration platform that solves a vast array of cross-org use cases and avoids the procurement of various point solutions that can be leveraged only by a subset of users.
From Theory to Practice: The Blueprint for Secure AI Workflow Collaboration
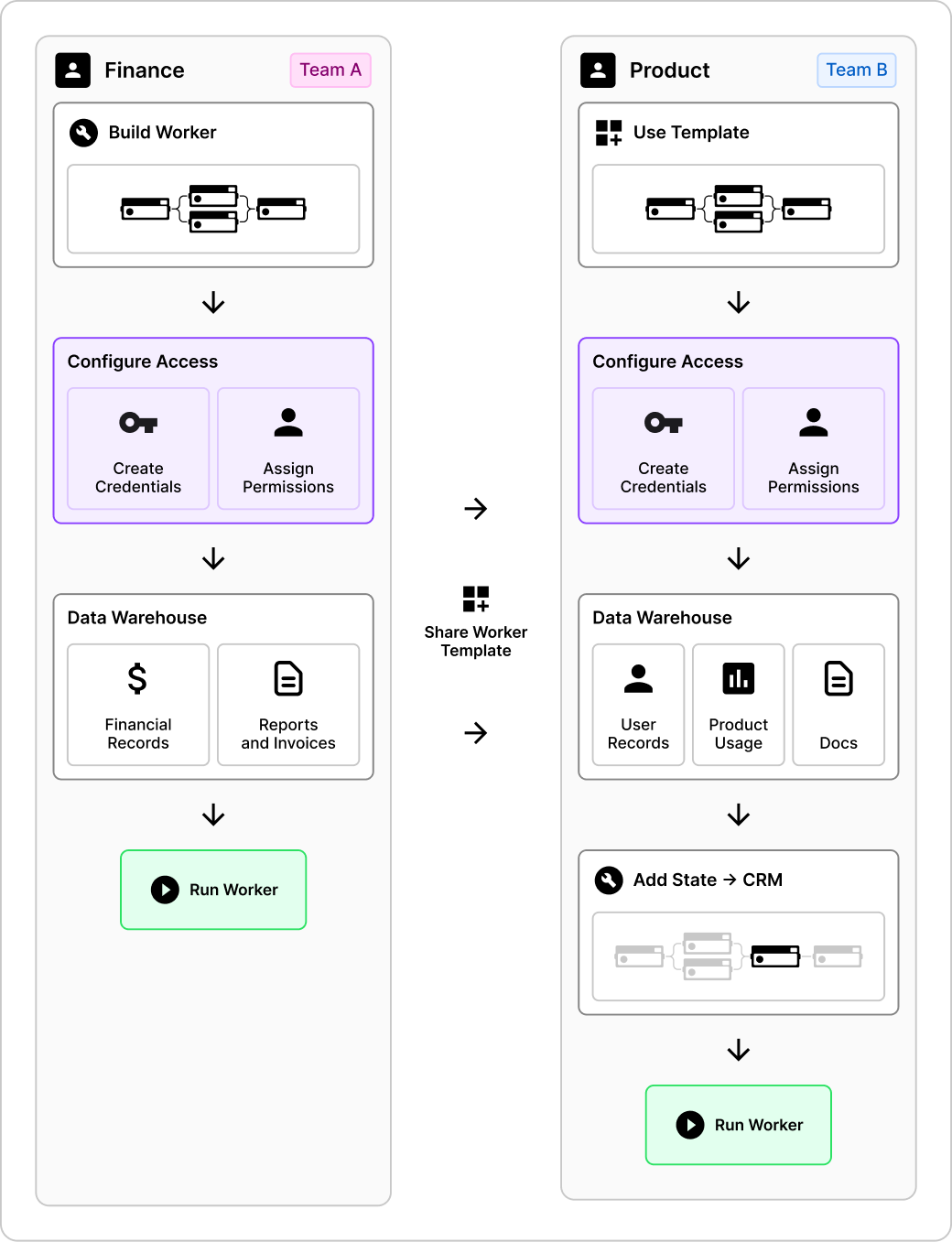
To make this tangible: Imagine the Finance team building a "Quarterly Performance Summary" Worker. They use their securely stored credentials to grant it access to resources in the internal data warehouse and their proprietary reporting tools. Using the SCIM-synced groups and assigned roles defined in the Lemma Platform, execution and resource permissions are restricted to the "Finance Leadership" team. The Worker's impact is enormous, saving dozens of hours each quarter from correlating data across different systems.
Soon, the Product team sees the Worker's value. They need a similar logic report, but focused on product-line revenue and feedback.
Under a traditional model, this would be a dead end. The Product team doesn't have (and shouldn't have) the same level and resource access as Finance. Rebuilding the logic from scratch would take days if not weeks.
With Lemma,
the path is simple.
1
Share the Logic, Not the Keys
The Finance team shares the workflow as a Worker Template. This copies the entire logical structure - the sequence of states and functions, the data transformations, the AI prompts - without any of the underlying credentials.
2
Re-Credential for the New Context
The Product team imports the template into their builder canvas and are prompted to add in their own credentials. They then plug in their own, scoped credentials for the data warehouse resource, which can only access product-specific schemas.
3
One-step Worker Adaptation
The Product team adds one new state to the Worker, adding customer feedback from their CRM and product insights tool.
4
Run Securely
They can now run the workflow. The logic is 90% reused, but the data it accesses is securely partitioned by their own needs and permissions.
This is the holy grail of enterprise AI transformation: reusability without risk. The intellectual property of the workflow logic is compounded across the organization, accelerating time to value, while data segregation and access controls are perfectly maintained.
Every step of this process happens inside a clear "glass box." Every human access, triggered Run, API call, and piece of data accessed is meticulously logged and is fully auditable. Giving information security and compliance teams the visibility they need to trust the system and verify that every action, whether taken by a human or an agent, is compliant and authorized.
An AI-First Future will Include a Hybrid Workforce
We are entering an era defined by a new hybrid workforce where humans and AI agents operate within the same systems to plan and execute complex tasks. Successfully managing the intersection of human and non-human identities is no longer just a security challenge; it is one of the most critical enablers for AI-driven business transformation.
Orchestrating authentication and authorization turns security from a gatekeeper into a strategic advantage. It provides the foundation of trust required to move AI from a series of fragmented initiatives to a secure, scalable, and compoundable engine that powers mission-critical operations and drives business success.
If you're grappling to establish a secure connection between your enterprise systems and the emerging applications for AI agents, we'd welcome you to connect with our team. We are passionate about solving these problems and can demonstrate how Lemma provides the secure foundation you need to unlock the strategic value of AI with confidence.